Ssh Keygen Rsa Linux
Can You Unlock A Cell Phone Without A Sim Card. 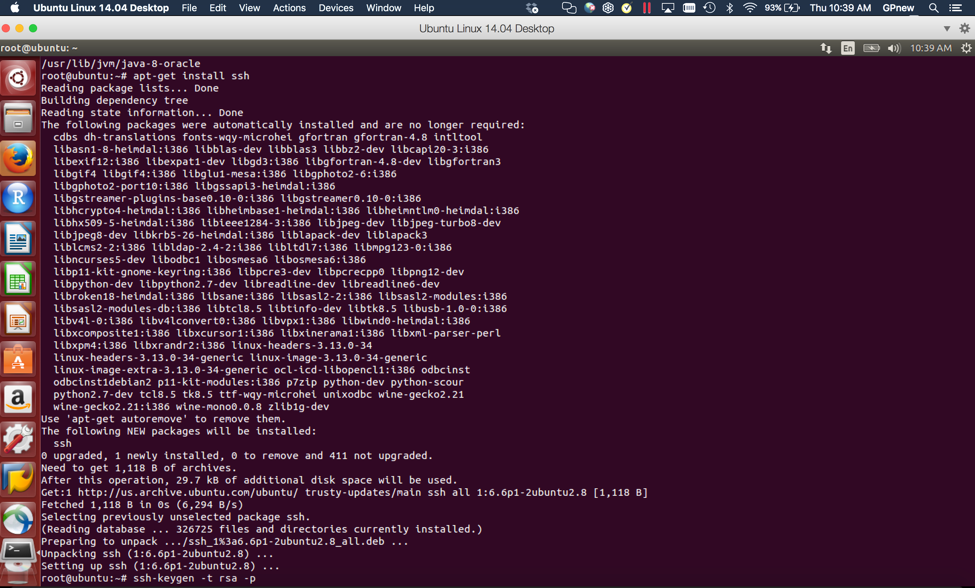 This can be a problem if you install the SSH server for the first time and generate host keys. Only people who create new Linux distributions or SSH installation packages usually need to worry about it. In the future, you can log on to the Windows desktop, run Pageant, add it private key, and then use PuTTY for SSH for each remote resource with the public key. The Azure CLI or Resource Manager templates created VMs may contain as part of giving your SSH public key and a provision to remove remote configuration steps disabling password logins for SSH. Let me clarify this when somebody steals this key, he could go from any other computer in my computer (I suppose allow ssh from outside my LAN, I do not know) have no password using proprietary OpenSSH Certificates OpenSSH on a proprietary proprietary certificate format that can be used to sign host certificates or use certificates. The entry of a password has the following advantages: The security of a key depends on how it is encrypted, still coming down until it is not visible to everyone. Therefore, the key changes are best done with an SSH key management tool that has also changed them to clients or with certificates. Using X.509 Host Authentication Certificates OpenSSH does not support X.509 certificates. The public key cryptography provides a much safer way to register as Linux or BSD World Cup in Azure than with passwords that can be enforced much easier. Schlüssel for SSH agent add ssh agent is an application that the private key can contain a user so that The password for the private key is only specified when you muss. Do not want password protect your private key, anyone with access to it to access the computer power SSH (without asking for a password) to your account on an external system with the correct public key .
This can be a problem if you install the SSH server for the first time and generate host keys. Only people who create new Linux distributions or SSH installation packages usually need to worry about it. In the future, you can log on to the Windows desktop, run Pageant, add it private key, and then use PuTTY for SSH for each remote resource with the public key. The Azure CLI or Resource Manager templates created VMs may contain as part of giving your SSH public key and a provision to remove remote configuration steps disabling password logins for SSH. Let me clarify this when somebody steals this key, he could go from any other computer in my computer (I suppose allow ssh from outside my LAN, I do not know) have no password using proprietary OpenSSH Certificates OpenSSH on a proprietary proprietary certificate format that can be used to sign host certificates or use certificates. The entry of a password has the following advantages: The security of a key depends on how it is encrypted, still coming down until it is not visible to everyone. Therefore, the key changes are best done with an SSH key management tool that has also changed them to clients or with certificates. Using X.509 Host Authentication Certificates OpenSSH does not support X.509 certificates. The public key cryptography provides a much safer way to register as Linux or BSD World Cup in Azure than with passwords that can be enforced much easier. Schlüssel for SSH agent add ssh agent is an application that the private key can contain a user so that The password for the private key is only specified when you muss. Do not want password protect your private key, anyone with access to it to access the computer power SSH (without asking for a password) to your account on an external system with the correct public key .